Statement in advance: this post includes personal account security and credential management, but it is just casual writing that includes some of my boring dailies. 😂 So please kindly do not regard this as a knowledge post.
Obviously, the Internet is becoming an inevitable part of our lives, and accounts are also becoming an unavoidable part of the Internet. Actually, long before, except for the service featuring individuals such as forum, game, E-mail, and game, we could utilize most Internet service providers (ISPs) without an account. The ISPs could use a tiny browser cookie to hold all the anonymous and temporary personalized contents. And at that moment, the ISPs didn’t desire much to dig personal information. 🤣 It was pretty easy to memorize all the credentials because nearly all the credentials are one combination of user name and password or random combinations of several user names and passwords. With the rapid development of the Internet and the growing desire for personal information, we need to create more and more accounts for signing up the ISPs. The more personal information the accounts include, the more cybercriminals target our accounts. So the ISPs issued many restrictions on passwords, and our old-school way didn’t work as well as before.
- The password needs updating periodically. – More backup passwords can handle this.
- The new password should not be the same as the several previously used passwords. – Fine! Let us prepare several passwords for rotation.
- Simple passwords are not allowed. – Cool. It seems we need to prepare several complicated passwords.
- The new password should not be the same as all the previously used passwords. – Are you kidding me?
Due to the above, this kind of conversation always happens between my wife and me.
My wife: I need to use XXXX for YYYY.
Myself: You need to signup before using XXXX for YYYY
My wife: Let me check.
One thousand years later…
My wife: It shows that I have already signed up for this before, but I cannot recall the password.
I helped her to retrieve the account and set a new password, then asked her again and again not to forget again. I was definitely sure that she would forget it again.
My wife: How do you memorize so many user names and passwords?
Myself: I cannot recall passwords either, even sometimes can’t recall the usernames…
My wife: So, how do you log in?
Myself: With the help of the password management tool.
My wife: It sounds complicated… Will try when I have time.
Myself 😓 …
This kind of conversation always happens periodically.
As more and more accounts need managing, I really cannot do that without a password management tool now. But I did manage with the rotation of several passwords for a long while because the password management tool was tough to use before:
- It couldn’t sync between devices. I should manage all the accounts on a specific device which I called the primary device. Then exported the accounts from the primary device and imported them into other devices. It seems pretty ridiculous in this period when everything can be clouded, but I really did this for quite a long while.
- It was not platform-crossed. At that moment, due to the unstable market distribution of web browsers and mobile operating systems, there seem several colossal mountains between Microsoft, Google, and Apple. And it was really hard to seek software that can be compatible with Mac, Linux, Windows, Android, and iOS, also compatible with Chrome and Internet Explorer. Not to mention finding a platform-crossed password management tool.
- Terrible user interaction (UI). It was not bad on PC because the tool could automatically fill in the user name and password via a browser extension. But when using it on a cellphone, it was really a nightmare. Can you imagine that the password management tool could only automatically fill in the user name and password when accessing the website with its built-in browser? I was the one that could not stand the build-in browser, so I had to use the copy-and-paste way to input the user name and password from the password management tool. Not to mention that some webmasters forbid copying and pasting on password textbox.
So after I had tried the password management tool for a short while, I reverted to the old-school way of password rotation.
Reading till here, I believe that some guys may wonder why this guy used so many different browsers and operating systems. Not for complicated reasons:
- At that moment, my office laptop is Mac. And my personal laptop is running Ubuntu and also Windows due to game compatibility.
- Due to the on-call policy, I brought one office cellphone and one personal cellphone. One was an iPhone, and the other one was an Android phone.
- Firefox is my favorite web browser, but before, I mostly used Chrome on Mac and Windows, and I used Chromium on Linux. But there are several unavoidable sites, such as bank sites and government sites, that only support disgusting Internet Explorer 6, so sometimes I still had to switch to IE.
Personal Credential Management
Since Chromium is getting more completed and the Firefox is more popular than before, most applications provide extensions for Chrome and Firefox. More and more of them also provide for Edge. Thanks to the Autofill and Accessibility of Android, and the AutoFill Passwords setting of iOS, I completely rushed to the password management tool again. After trying several options, Bitwarden is my final choice because:
- It can sync between devices, so I can manage all the accounts on any device.
- It provides extensions for Chrome, Chromium, Firefox, and Safari. This totally meets my requirements.
- It supports both iOS and Android.
- Even though some ISPs leaked the accounts, different passwords for different accounts can significantly prevent credential stuffing.
- The free version is good enough.
With the help of the password management tool, when I sign up for an ISP, I can use the password generator to create a complicated password instead of figuring it out by myself. I usually tick all the options to make sure the generated password can meet all the requirements of different ISPs.
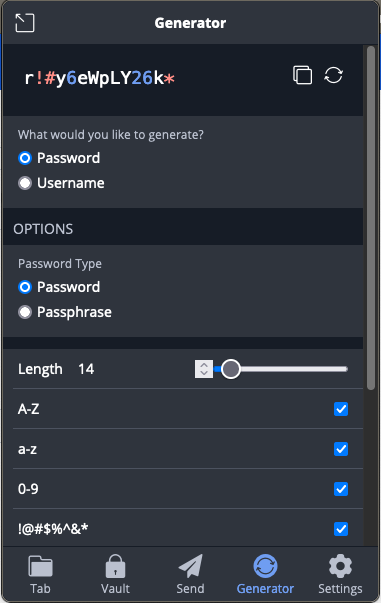
When you use the generator to get a password, you can also let Bitwarden save it in its vault automatically. From then on, Bitwarden can help us fill in the user name and password of this ISP account, so we no longer need to memorize the complicated password. This way, the passwords of different accounts are totally different, which can significantly prevent credential stuffing.
Personal Account Security
Password management tools are really helpful but will also lead to a problem. It is that if the Bitwarden account is hacked, does it mean that all the accounts will be hacked? To explain this, we need to break this down into two questions:
- How do we minimize the Bitwarden account theft? Because Bitwarden is the portal of all the accounts, we can’t set an extremely complicated password for Bitwarden.
- If the Bitwarden account is hacked, how do we ensure all the accounts in the Bitwarden vault can not be easily hacked?
Two-factor authentication (2FA) can help us.
Multi-factor authentication (MFA; encompassing authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects user data—which may include personal identification or financial assets—from being accessed by an unauthorised third party that may have been able to discover, for example, a single password.
Wikipedia
Based on Wikipedia and above, in a nutshell, besides providing the user name and password, the user needs to provide at least one more piece of evidence before getting access to the account. For example:
- OTP SMS. This is quite popular for 2FA, and sometimes it becomes the first authentication method. To be honest, using OTP SMS as the first authentication method without 2FA is really a bad idea. If your phone is lost, someone can take SIM out of your phone, easily get your contact number, and log in to your account with OTP SMS without unlocking your cellphone. So to prevent this, I have enabled SIM lock on all of my SIMs. That is to say that if my cellphone is rebooted or the SIM is put into a new cellphone, the SIM will not work, and the cellphone will show no signal or service. If the PIN has been wrongly input three times, the SIM will be locked unless you can provide a correct PUK or get a new SIM from the carrier.
- OTP E-Mail.
- OTP generated by authenticator APPs. Microsoft Authenticator and Google Authenticator are the most popular. I recommend the former one because it can sync between devices. Once my cellphone malfunctioned, I could not get the OTP via Google Authenticator to log in to an account containing some important historical information. The support was quite “dedicated” and refused to reset my Authenticator binding, even after I provided my user name, password, E-Mail address, and a list of previous login locations and timelines. 🤦♂️
- The recovery codes when binding Authenticator. Please do take note of that unless you can make sure you will not lose the bound Authenticator, or you will face the same issue I mentioned above.
- Security keys. I will explain later.
Let’s get back to the first question. How do we minimize the Bitwarden account theft? Enable the 2FA of the Bitwarden account.
The answer to the second question is the same. Enable the 2FA of all the accounts if ISPs support 2FA.
Issues when 2FA is enabled
Conclusion first:
- Please ensure you enable at least two different 2FA methods if the ISPs support them.
OTP SMS is quite convenient until you would like to update your contact number. I needed to update my contact number once due to relocation to another city, and I couldn’t recall all the ISPs binding my previous contact number, so I could not update the contact number of all the accounts. Even if I could recall, it would be horrible to update all over again. Now with the help of the password management tool, I can easily list and categorize all my accounts. For example, all the accounts binding my China contact number are sorted out; all binding my Singapore contact number are in another category, all binding security keys are sorted out, etc. Also, I activated at least two 2FA methods to ensure I don’t need to update all the account security settings immediately.
- Try not to use commonly changing 2FA methods, such as contact numbers. Instead, I prefer E-Mail and security keys.
- If commonly changing 2FA methods are not avoidable, make sure you have a backup method. Mainly I bind two contact numbers on my essential accounts. Significantly I bind two if security key authentication is enabled because security keys cannot be duplicated in a usual way. I take one with me and put one in a safe.
Security Key
Mentioning security keys, it was back to my university days. The bank industry was really backward, so online and mobile payments were unavailable yet, and even credit cards were not expected. We should pay via cash nearly everywhere.
Nearly by the end of my university life, several banks, such as CMB, released the online payment and online transferring. But the processes were really complicated. Whenever I would like to do this, I had to meet four requirements:
- Windows OS. So I had to install a Windows virtual PC on my MacBook.
- One management software that the bank provides, and it only supports Windows OS.
- Internet Explorer. Because the bank password input component is an ActiveX controller that only supports IE.
- One Dongle named U Key can only be used to operate bank accounts.
Due to the complexity of the operation and lack of requirements, I mostly prefer doing the transfer via ATM. And due to low utilization, I lost the U key twice when I moved to a new dormitory or accommodation. If I would like to apply for a new one, I needed to apply to disable the lost one first. The application for a new one could only be processed 24 hours after the application to disable. It meant I needed to bring lots of documents to the bank twice. Terrible!
I updated my contact number again after arriving in Singapore. And this made me think about trying a security key again. It looks amazing that there are tens of security keys supporting Universal 2nd Factor (U2F). Supporting U2F means that I use one security key as the 2FA method for nearly all my accounts and don’t need to assign each account a different key. Finally, I chose YubiKey after going through lots of reviews. If you have difficulties selecting a suitable model of YubiKey, you can use this chooser provided officially. 😂 You can also choose an appropriate security key from the list above.
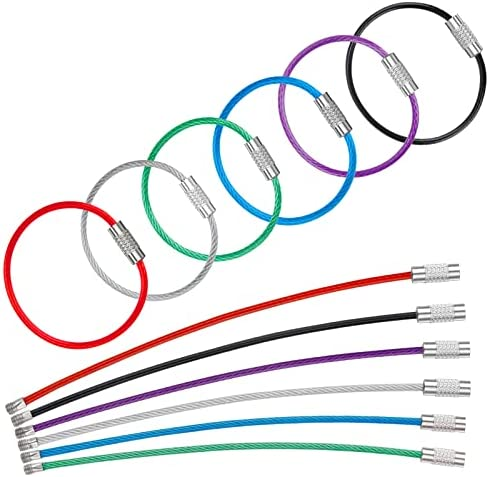
If you would like to use a security key to authenticate on your cellphone, please choose the NFC model. Because most apps can now read security keys via NFC, you can simply tap your key on the back of the cellphone to authenticate.
One tip. If you choose the NFC model, I highly recommend using this kind of steel cable keychains as below. If you still use the common hard steel ring keychain, it will affect the NFC reading of the cellphone because the keychain will block the key totally adhering to the back of the cellphone.
As a security key, its ability is far beyond account login. For example:
- It can authenticate the PC login, that is to say, that you need to plug in the key to finish the login after starting the PC. After all, the theft of thesis and dissertation is not rare anymore. Of course, if your document is important enough to enable the security key for the PC login, don’t forget to encrypt your disk in case someone takes your hard disk out of your PC. 😂
- With an NFC module and a digital lock supporting open source home automation, you can use a security key to unlock the door.
- Of course, we can also use an outdated NFC-supported cellphone as an NFC reading module to create more exciting ideas with an open-source home automation application.
- It can manage your GPG key for passwordless SSH login and passwordless Github repo operations.
The above is just to throw a brick, and you can dig more.